At KEYSYS we know software & technology are ever-evolving landscapes. That’s why we started the KEYSYS Development Book Club to help our team grow and improve in our core values of Knowledge, Constant Improvement, & Collaboration.
Each Wednesday our development team meets together to discuss a chapter in the book they’re reading and work through examples together. These meetings have really helped our team and culture grow as everyone has the chance to improve together.

This is the second of two blog posts (read part 1 here) describing the first book featured in the KEYSYS Development Book Club: Building Microservices with ASP.NET Core by Kevin Hoffman. Hoffman’s book outlines some essential features of .NET Core, including request and response handling and third-party dependency management. Hoffman also provides more in-depth architectural guidance, such as how to isolate business code for unit testing. Most importantly, the book presents all these details in the context of cloud-native application design, explaining how to structure services for event sourcing, service discovery, telemetry, and more.
This book inspired us to use secure environment variables to override application configuration files, resulting in secure and streamlined deployment pipelines.
Managing Application Configuration with Secure Environment Variables
In his book, Hoffman highlights .NET Core’s ability to use environment variables to securely override configuration file values. This means that deployment pipelines can pull sensitive configuration details from a secret key store and then write them to local environment variables that override .NET Core’s configuration file. The sensitive details are never stored in source control, meaning they are less likely to be stolen or used irresponsibly. Additionally, developers can still set the configuration file to suit their local needs as before.
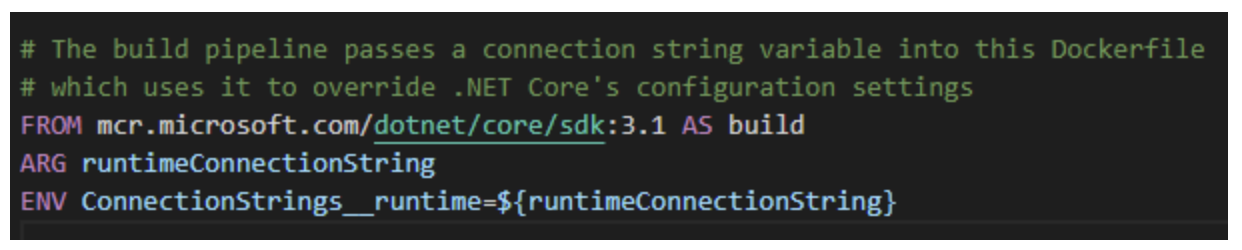
After learning about this capability in Book Club, we implemented it in our .NET Core microservices and end-to-end automated testing solutions. Now, the secure configuration details for these projects aren’t stored as plain text in source control, but deployments can still be easily automated via pipelines.



